- Solution area:Organisations ,Processes ,Quality assurance and certification ,Social participation and engagement ,Technological innovation ,
- Аdministrative level:State ,Federation ,
- Solution process:Digitization and technology ,Public service ,Science and research ,
- Technology:Artificial Intelligence ,Automation and robotics ,Information technology ,Networks ,

Cyber Security Operation Center
The central hub for digital security
In an increasingly connected world, cyberattacks and digital threats are omnipresent. Companies, organizations, and public institutions must protect their critical infrastructures, sensitive data, and business processes around the clock. A Cyber Security Operations Center (SOC) provides the necessary expertise, technology, and organizational structure to detect threats early and respond effectively. It raises awareness of security-critical situations and strengthens digital resilience at all levels.
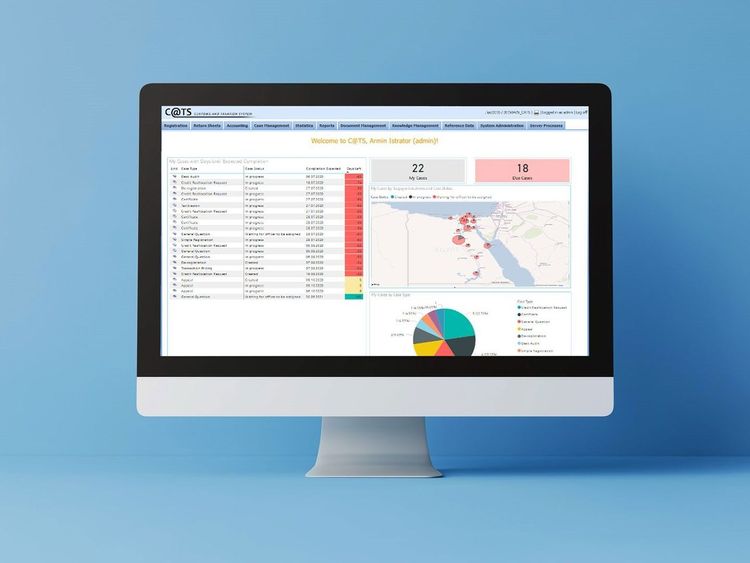
Quick Facts
How it works
The Cyber Security Operations Center combines organizational processes, technological tools, and expert knowledge. Participants receive comprehensive training on the setup, objectives, and organization of a SOC, with a focus on IT and OT systems in companies and critical infrastructures. Key components include working with technical systems such as Intrusion Detection Systems (IDS), Security Information and Event Management (SIEM), and Security Orchestration, Automation, and Response (SOAR). The training also covers practical content on current cyber threats, technical vulnerabilities, incident response, playbook development, and digital forensics. At AIT’s in-house Cyber Range Training Center, a specialized simulation and training environment, participants can apply and deepen their skills in realistic scenarios under the guidance of experienced trainers. This enables them to detect threats, analyze security incidents, implement preventive measures, and continuously improve IT security.
The Big Picture
With a Cyber Security Operations Center, organizations increase their digital resilience, improve security monitoring, and minimize the risks of cyberattacks. The structured combination of knowledge transfer, technological tools, and hands-on practice equips employees to recognize threats early and respond efficiently. This ensures the uninterrupted operation of critical systems, protects sensitive data, and strengthens the trust of customers, partners, and the public. At the same time, the SOC supports compliance with legal requirements, internal standards, and best practices in information security.
Image: © Freepik.com